Overview:
Configuration of VMWare ESXi Networking / vSwitches
Since I built my physical lab (initially for my CCNA) 2-3 years ago, I have struggled to keep the hardware and software up to date due to many factors such as cost, noise, physical space and power consumption. Another attractive aspect is the variety of networking appliances that can be deployed and ran on demand.
As a result of this I recently (last year) moved my focus to running virtual appliances where possible (mainly using trials) on my VMWare ESXi 5.5 Host. My Host consists of 64GB of RAM . 2 x Dual Port NICs and adequate Dual Xeon processors to allow me to run a variety of topologies integrated with physical hardware for features that are not easily virtualised.
What is a vSwitch?
A vSwitch in ESXi is a virtual switch which connects virtual machines on a virtual network to a physical network, this is done through uplink adapters called vmNICs. vSwitches ignore Spanning Tree BPDUs on the uplink as the ESXi hypervisor uses a split-horizon mechanism between uplinks; this is where frames received on one uplink can’t be sent to another uplink resulting in a ‘loop.’
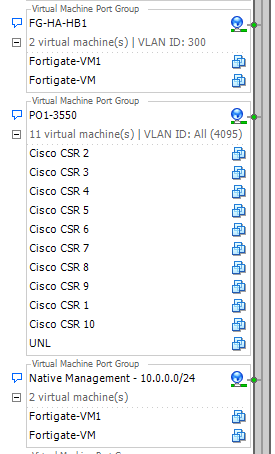
A vSwitch connects in a conventional manner by trunking over multiple VLANs from a physical switch, a port group can then be created for one of three example scenarios, the vNICs on the VMs then assigned to the port group as below :
- VLAN Port Group – vNICs that are assigned to this port group are untagged (access ports in cisco world) members of the VLAN specified on the port group, e.g. VLAN 900. This is useful when a Virtual Appliance, such as a Juniper vSRX, doesn’t support VLAN Tagging.
- Tagged Port Group – vNICs that are assigned to this port group are tagged (cisco: trunk ports) with the specified VLANs in the port group. This type of group is used to ‘tag’ the VLANs over from your physical switch. vNICs can be assigned to this port group and 802.1q sub-interfaces / units can be created ‘tagging’ a VLAN per sub-interface on the VM.
- Untagged Port Group – vNICs that are assigned to this port group receive untagged traffic (native VLAN) from the physical network as specified on your physical switch uplink, this is alongside side no VLAN specified (0) on the port group
Configuration Overview:
The current relevant part of the setup is a 2Gb (2x1Gb) Cisco Etherchannel link from my ‘core switch’ to my ESXI Host vSwitch; LACP is not supported by vSwitches. This switch contains the VLANs that are routed by both the VM Appliances and also physical devices.
Switch Configuration:
The relevant ports on the cisco switch as configured as below:
interface GigabitEthernet0/1
switchport trunk encapsulation dot1q
switchport trunk native vlan 999
switchport mode trunk
switchport nonegotiate
channel-group 1 mode on
interface GigabitEthernet0/2
switchport trunk encapsulation dot1q
switchport trunk native vlan 999
switchport mode trunk
switchport nonegotiate
channel-group 1 mode on
interface Port-channel1
switchport trunk encapsulation dot1q
switchport trunk native vlan 999
switchport mode trunk
switchport nonegotiate
spanning-tree portfast trunk
spanning-tree bpdufilter enable
ESXi Host VSwitch Configuration:
- Click on Host IP > Configuration > Networking > Add Networking > Virtual Machine
- Select your Uplink Adapter
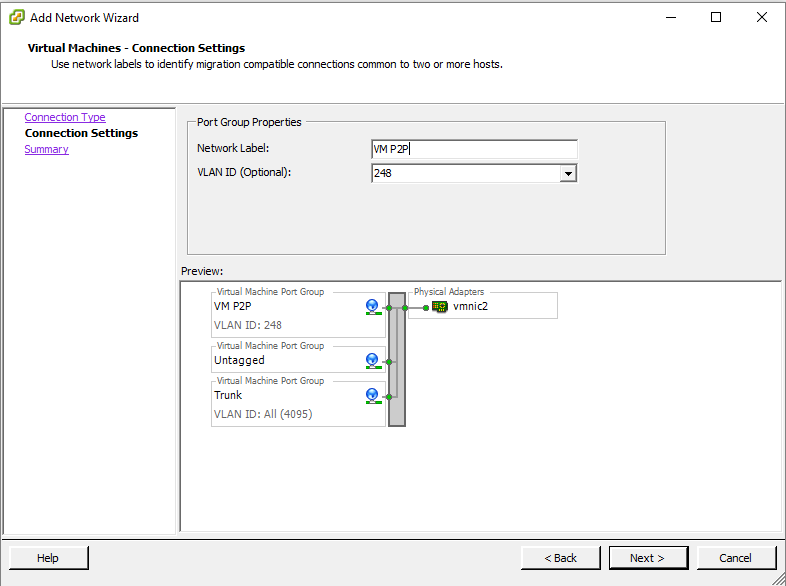
Create your Port Groups here, default one is set for untagged traffic, repeat this step add further port groups, this is how it should look on the last of three.
The image below is for reference, I have used a spare NIC.
ESXi Virtual Machine(s) Configuration:
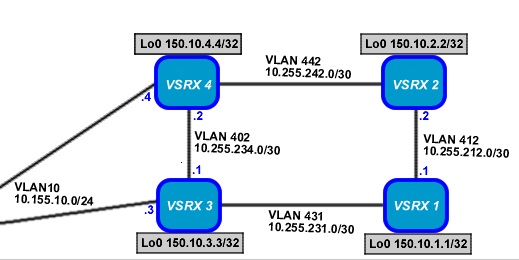
You can now add your vNICs to the relevant port groups and configure the interfaces in the VM itself. Here’s a partial diagram of my vSRX appliances which connect to my Cisco CSR Appliances:
Each node above represents a VM and each link represents a common VLAN. Since the vSRX doesn’t support VLAN tagging, an individual port group exists for each VLAN, the respective interfaces of each node are added to the appropriate port group and configured.